Retail Attacks: The Cause and the Cure

In the past decade, the payments industry has made technological leaps and bounds, but one thing has remained the same—the looming threat of retail attacks. In fact, according to the Privacy Rights Clearinghouse, “more than 260 million retail records have been reported as leaked, lost or stolen in the US since 2005.” Shockingly, over 99% of these compromises resulted from the manipulation of an endpoint or the use of malware.
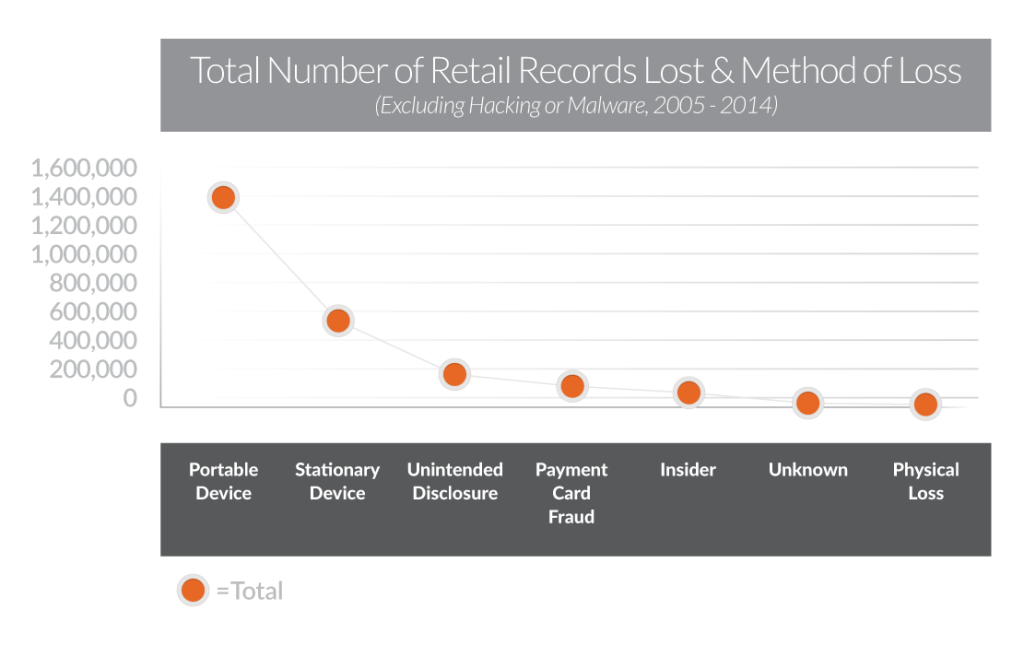
Overview of the total number of retail records lost and methods of loss (excluding hacking or malware) in the US since 2005
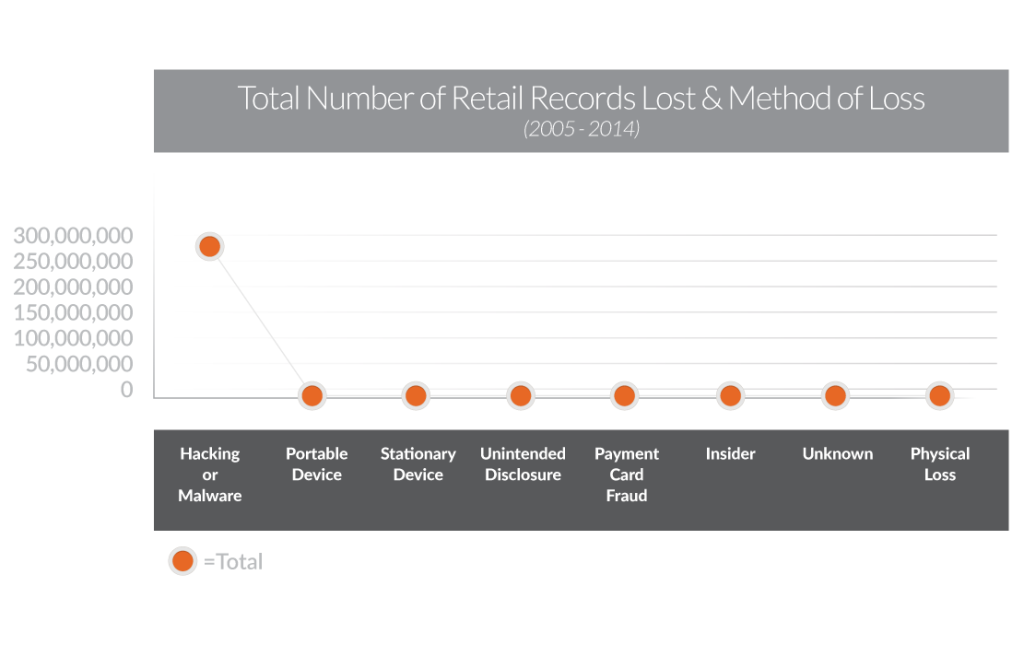
Overview of the total number of retail records lost and methods of loss in the US since 2005
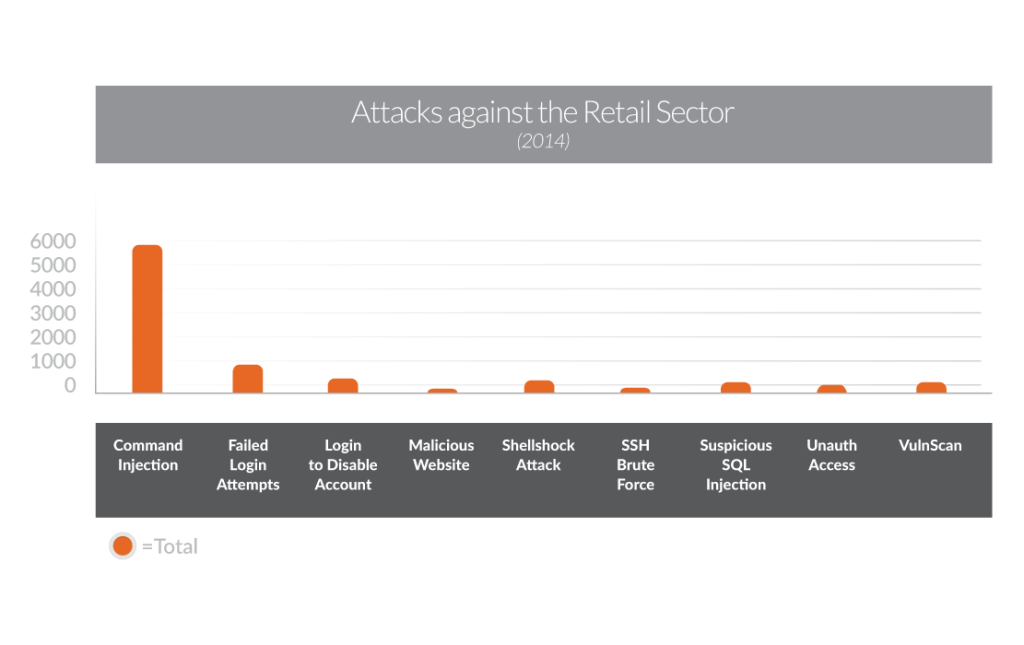
Overview of the total number of attacks against the retail sector in 2014
As the first graph demonstrates, POS systems are frequently infiltrated by criminals who use malware as their weapon of choice. Simply put, malware seizes a payment card’s track 1 or track 2 data that is housed on the card’s magnetic stripe. Once this information has been acquired, criminals are able to re-code the data onto counterfeit cards.
In order to combat retail data loss, it is important to understand the different methods in which data is exploited. This blog will primarily focus on today’s most prevalent types of POS malware and following methods of attack—Command Injection and Shellshock—in addition to how CardConnect can help you defend yourself against an attack.
Common POS Malware
BlackPOS
This particular POS malware was used for The Home Depot breach and was uncovered by the Russian security company, Group-1B in March of 2013. Black POS scans the memory of track 1 and 2 credit card data that is stored in a merchant’s system. Once the data is retrieved, it is housed in a file (called output.txt) and transferred to a FTP server.
Dexter
Dexter is a Trojan horse that was disclosed by the Israeli cyber security firm, Seculert in December of 2012. Dexter scans a system’s memory in search of track 1 and 2 card data. Once retrieved, it uses HTTP communications with a command and control (C2) server to transmit card data and receive updates.
Vskimmer
McAfee disclosed Vskimmer in March of 2013 and unlike Black POS and Dexter, only searches for track 2 data. It uses HTTP to transfer stolen card data to a C2 server. If a criminal is unable to connect to the Internet, Vskimmer can be set up to copy data to a USB device.
Alina
Alina is a Trojan horse that was exposed by the SecureWorks Counter Threat Unit (CTU) in March of 2013. It searches running processes for credit card track data, and uses HTTP and a C2 server to upload stolen card data and download updates.
Citadel
Citadel is a widely used malware kit that compromises online banking and credit card data. It is used to track an individual’s web browsing movements and contains a variety of implanted features that allow criminals to locate and infiltrate POS systems. Citadel also gathers information about the different types of software that are installed on a compromised system; criminals can then harvest this data.
Command Injection
Command injection is used to infect a web page with an HTML code that is implanted by a hacker. When users visit the infected page, their browsers translate the code, which results in the deployment of attack commands against the users’ computers and associated networks. The absence of data validation executed by POS and e-commerce security administrators makes command injection a popular method of attack in the retail area.
Shellshock
Shellshock attacks have become increasingly popular since September of 2014. These attacks affect the GNU Bash shell and exploit a 20+ year-old bug (referred to as Shellshock) that exists within the system. Bash is a program that is commonly used on Linux, Solaris and Mac OS systems to implement command lines and command scripts. Overall, these systems use Bash as a command and a command interpreter. With that being said, a hacker can manipulate the bug to allow remote implementation of arbitrary commands on computers and servers with no authentication required.
—————————
P2PE: Your Solution to Retail Attacks
Retail attacks show no signs of stopping, so it’s important for merchants to make sure their technology is malware resistant. Point to point encryption (P2PE) is an important step in the right direction when it comes to protecting against cyber criminals. P2PE encrypts cardholder data before a transaction is executed so the merchant will never come in contact with sensitive cardholder information, thereby cutting off a potential hacker’s access to vital personal information. As a result, our merchants are able to conduct business with the confidence that no unencrypted cardholder data will be stored in their system–not even for a moment. Combined with tokenization, the two technologies are an unbeatable pair against card fraud. Learn more here.

